Apps
Overview
The Apps feature helps Kolide administrators discover and protect work-related web applications used by employees across their organization.
App Discovery aggregates data from usage sources such as browser activity and desktop app installations to identify which web apps employees commonly use and where company data may be stored.
Extended Device Compliance allows administrators to notify end users about device health issues and impede access to work-related apps using the 1Password Browser Extension – whether or not they support SSO.
Managed App Instances allow administrators to protect individual Google Workspace SAML SSO-configured applications, and makes sure only devices that are known and secure can authenticate.
Discover Web Apps
Select Apps in the Kolide navigation menu to open the Discovered tab of the Web Apps page. This provides an overview of apps Kolide has detected usage of by your team members.
The Discovered apps page is like an inbox – as you reason about the apps Kolide finds, you can move them from their initial status of Discovered to Accepted, Rejected, or Ignored.
On the overview page you can:
- Review a list of all apps Kolide has discovered usage of across your organization.
- Discover unfamiliar apps and learn what they might be used for.
- Determine popularity of discovered apps by the number of people using them.
- Review apps’ data risk scores to evaluate which apps represent the greatest concern.
- Assign a status or configure Extended Device Compliance for applications by clicking the checkbox next to an app’s name.
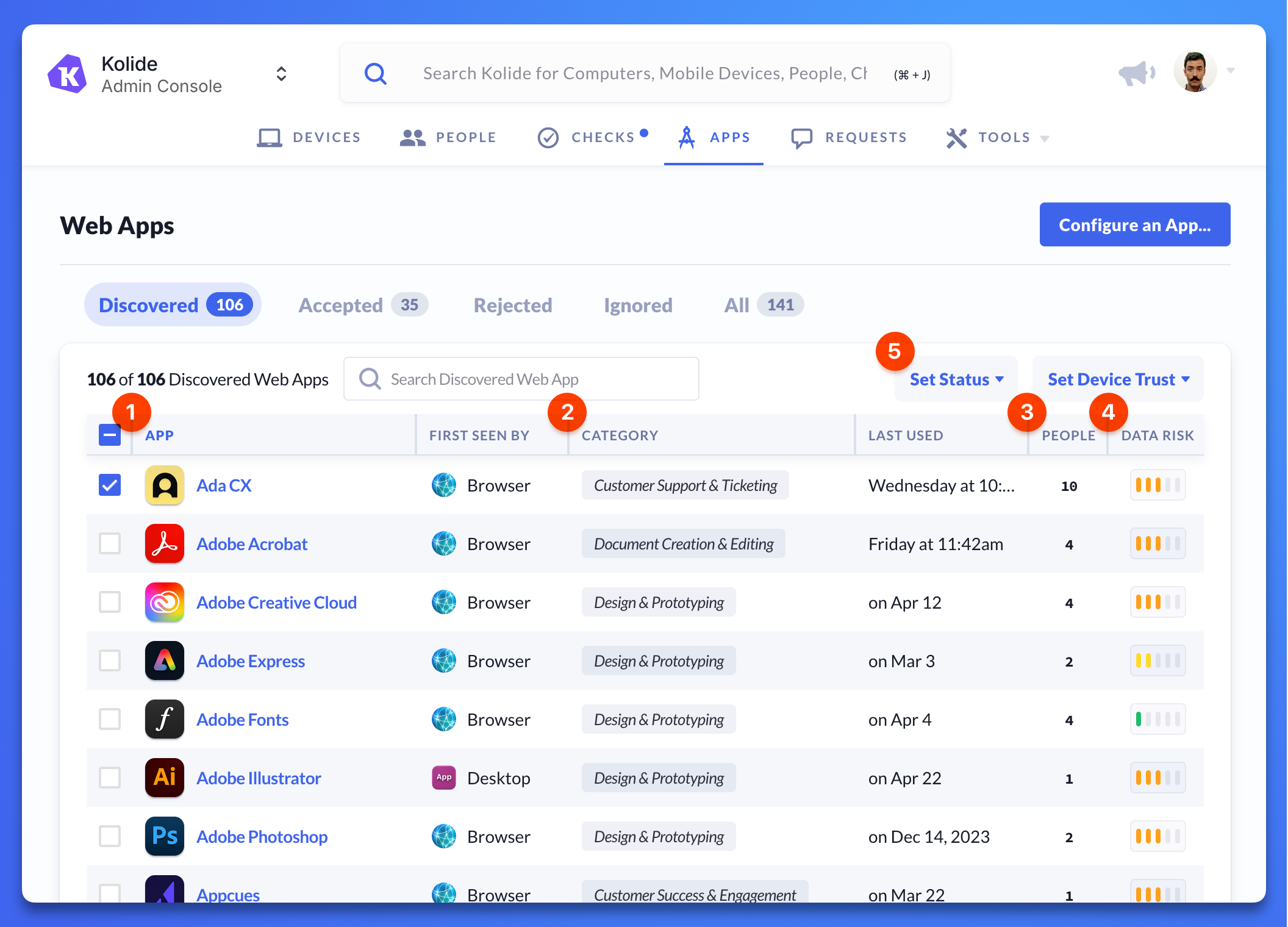
The Discovered Web Apps page in Kolide showing examples of apps that have been detected.
From the Discovered apps overview, you can click on any individual app to open its detail page. This detail page provides a description of the app, suggestions about the types of data it may process and store, and a detailed breakdown of its usage across your employees, such as how often it is used and when each employee last used it.

How usage is determined
Kolide determines web app usage through on-device queries run by its agent. These queries retrieve a count of total visits the end user has made to work-related web apps in their browser, and also detect installations of companion desktop apps (for example, Grammarly Desktop). Kolide makes sure app discovery preserves your employees’ privacy by limiting what data is collected, and scoping that collection to only apps belonging to a pre-defined list of work-related web apps.
Kolide-detected usage information is an estimate only. It does not capture browser visits that are made via Private Browsing or Incognito sessions. It will also not report any visits made that were subsequently cleared from the browser’s history.
Learn more about how Kolide limits its data collection to preserve employee privacy.
Assigning a Status to a Web App
You can assign apps one of four statuses: Discovered, Accepted, Rejected, and Ignored.
When Kolide first detects an app, it automatically marks the app as Discovered, unless you’ve preconfigured the app with another status. To preconfigure an app with a status of Accepted, Ignored, or Rejected, select the Configure an App… button at the top right of the page.
To set a status for an app:
- Select the checkboxes next to one or multiple apps.
- Select the Set a Status dropdown and choose a status.
Alternatively, you can click into an individual app’s detail page, then select the Mark App As dropdown and choose a status.
You can choose one of the four following statuses:
- ⚪ Discovered: Web apps your team members are using that match Kolide’s pre-defined list of business-related apps. You can review discovered apps and choose if you want to protect them with Device Trust. (Only apps with discovered usage can be set to this status.)
- 🟢 Accepted: When you turn on Device Trust for an app, it will be automatically marked Accepted. Marking an app Accepted does not automatically turn on Device Trust.
- ⚫ Ignored: If you don’t want an app to appear in your Discovered apps list, select Ignored. The app will be moved to the Ignored apps list on the Web Apps page, and you can choose to accept or reject it at a later date.
- 🔴 Rejected: If you aren’t interested in adding Device Trust to an app, select Rejected. When you mark an app Rejected, Device Trust is automatically turned off for that app.

App Data Risk
Each web app has an associated data risk level. You can sort by data risk to quickly identify which apps may be important to protect with Device Trust. Kolide uses the following labels to categorize data risk:
| Data risk level | Description |
|---|---|
| 1: Non-sensitive data | Publicly available, minimal risk |
| 2: Low sensitivity | Basic internal data, general operations |
| 3: Moderate sensitivity | Internal business data, non-critical personal data like names or emails |
| 4: High sensitivity | Intellectual property, customer data, significant impact if exposed |
| 5: Critical sensitivity | Financial records, PII, legal documents, or anything that could cause major business harm |

Privacy Center
As part of the Discovered Apps feature, end users will see a “Web App Activity" section in their End User Portal - Privacy Center.

The Web App Activity section shows the end user which web apps Kolide collects usage information for. Kolide defines 200+ work-related web apps, and only collects usage metrics related to those specified apps. The pre-defined list of apps cannot be expanded or changed by an administrator with Kolide access. New apps are only added by changing the Kolide source code, which is subject to rigorous code review.
To access the Privacy Center, select your profile in the top-right corner of Kolide, then select My Device. Next, select the security camera icon. You can also follow the link below:

Extended Device Compliance
Requirements
This feature is currently in Early Access Preview, and has the following requirements:
- Requires a 1Password Business Account
- Requires the Nightly version of the 1Password browser extension in a Chrome-based web browser (for example Google Chrome, Chromium, Microsoft Edge, Brave, Arc, etc.).
For more information about configuration requirements and testing Extended Device Compliance, see our Extended Device Compliance Quick Start Guide.
Overview
Extended Device Compliance allows you to extend device health checks to the non-SSO managed and unmanaged web applications your employees use for work.
When your team members attempt to access protected web apps, the 1Password browser extension checks their device health using Kolide and provides self-serve remediation instructions for any failing Checks directly within the browser. If your team members don’t resolve failing Checks within a specified time frame, the 1Password extension obscures the underlying page, impeding access to the app until the user fixes the problem.
Extended Device Compliance will interrupt and block access to protected apps even if the end user is already signed in.
You can turn on Extended Device Compliance for an individual app by opening the app details page and toggling on Extended Device Compliance.
You can also turn on Extended Device Compliance for one or many apps on the Web Apps page:
- Select the checkbox next to the app in the Discovered Web Apps list.
- Select the Configure Extended Device Compliance dropdown, then select Enabled.

Extended Device Compliance can be enabled for a single app, or for multiple apps at a time.
After you’ve turned on Extended Device Compliance for an app, Kolide will block or interrupt access based on the Blocking strategy you configured for any of the failing Checks detected.
Notification States
There are 3 different states that people can encounter when they fail a Check.
-
Notify Only - The 1Password browser extension shows a pop-over notification in the top right of the active tab informing the end user that they have an issue with their device. The user can still see and interact with the webpage underneath the pop-over. The user can defer the notification without fixing the failing Check by selecting the button labeled Fix later.

-
Will Block - The 1Password browser extension shows a pop-over notification in the top right of the active tab informing the end user that their device will be blocked in
xdays if they do not fix their failing Checks. The user can still see and interact with the webpage underneath the notification. The user can defer the notification without fixing the failing Check by selecting the button labeled Fix later.
-
Blocked - The 1Password browser extension obscures the webpage with a blur overlay and shows a pop-over notification in the top right of the active tab informing the user that they cannot access the web app until they fix their failing device Checks.

Fixing Device Issues
When a user clicks an issue in the notification, the 1Password browser extension directs them to the Kolide End User Portal where they can see more details about the failing Check as well as instructions for how to self-remediate the issue.

The Kolide End User Portal serves contextual fix instructions which guide end users in self remediating issues on their device.
Once the user fixes the failing Check, the notification updates to let the user know that their device is “All good” and the notification can be dismissed. If the device has multiple failing Checks and only some are resolved, the notification will update to show the partial state of completion.

Managed App Instances
Managed App Instances are individual configurations of Google SSO-managed, SAML-compatible, web apps that can be protected with Device Trust.
When you create a Managed App Instance, end users will complete an additional step when they attempt to sign in to the app. After entering their username and password or providing their passkey, users will be redirected to Kolide Device Trust, which will verify that the device is registered and passing all configured Checks before allowing them to sign in.
Configuring a Managed App Instance
You can configure a Managed App Instance using the preexisting templates in the Apps catalog, or by creating a new Custom App. Both methods are detailed below.

Step 1: Add an App
Add an App From the Apps Catalog

- In Kolide, select the item labeled Apps in the top navigation.
- Select + Add Application. If you’re a Core or Connect customer, select Configure an app.
- Search or scroll to find the app you want to add, then select it.
- Optionally edit the app’s name, description, or icon.
- Choose whether you want the application to be visible in the 1Password browser extension app launcher or the Kolide End User Portal.
- Select Next Step.
Add a Custom App

If the SAML app you want to create a managed instance for doesn’t exist in Kolide’s Apps catalog, you can add it manually:
- In Kolide, select the Apps tab.
- Select + Add Application. If you’re a Core or Connect customer, select Configure an app.
- Select Add Custom App.
- Enter the name of the app. Optionally, add a description and custom icon.
- Choose whether you want the application to be visible in the 1Password browser extension app launcher or the Kolide End User Portal.
- Select Next Step.
Step 2: Configure App Settings
To connect your app to Kolide, you’ll need to copy and paste configuration details between the two. If you’re adding an app from the Apps catalog, select the Docs button to learn where to find your app’s configuration details. If you’re adding a custom app, check your app’s documentation. Configuration setting names can vary by app.

Provide Your App’s Configuration Details to Kolide
- Copy the Entity ID from your app and paste it into the Entity ID field in Kolide.
- Copy the ACS URL from your app and paste it into the ACS URL field in Kolide.
- If your app’s Audience URI is the same as the Entity ID, leave the Audience URI field blank. If the Audience URI field is different from the Entity ID, copy the Audience URI from your app and paste it into the Audience URI field in Kolide.
- Copy the Response Host (name of the service provider) from your app and paste it into the Response Host field.
- If your app requires the SAML response to be signed for authentication, select the checkbox next to Sign Response Body. Check your app’s documentation or configuration requirements to determine if this setting is necessary.
Provide Kolide’s Configuration Details to Your App
- Copy the Entity ID (Issuer) from Kolide and paste it into the Entity ID (Issuer) field in your app.
- Copy the Sign On URL from Kolide and paste it into the Sign On URL field in your app.
- Copy the Metadata URL from Kolide and paste it into the Metadata URL field in your app.
- Copy the Signing Certificate from Kolide and paste it into the Signing Certificate field in your app.
Optional App Settings
If your app allows signing AuthnRequests or requires sending information like Name ID Format, Single Sign-On URL, or Logout URL, add them to the Optional Settings fields in Kolide.